The Cybersecurity and Resilience Bill is a proposed legislative framework intended to strengthen the UK’s digital defences against evolving cyber threats. Through policy proposals focused on enhanced security measures, clearer accountability, and improved incident response, the bill aims to reduce national cyber risk and improve organisational resilience. The focus is both preventive and reactive, ensuring organisations are equipped to respond to incidents swiftly and effectively.
Understanding the Cybersecurity and Resilience Bill
What the bill addresses and why it matters
The Cybersecurity and Resilience Bill responds to the increasing frequency and scale of cyber attacks in the UK. With critical national infrastructure, government, and private sectors all vulnerable, the bill seeks to establish more consistent cybersecurity expectations and coordinated response mechanisms across essential services.

Visual representation of the UK Cybersecurity and Resilience Bill: mapping sectors covered and legal mandates.
Key Takeaways:
- The bill aims to establish baseline cybersecurity expectations for essential services.
- Proposals include stronger incident reporting and improved national response coordination.
- Applies to sectors including energy, healthcare, transport, water, and government.
Drivers behind the bill
According to the UK Government’s 2024 cybersecurity review, attacks targeting critical infrastructure have increased by 27% since 2021 (Source: UK Cabinet Office, 2024). In my experience with industry stakeholders, there is heightened concern surrounding ransomware, supply chain vulnerabilities, and insider threats. The rise of state-backed cyber activity adds urgency to legislative action.
Core obligations and who must comply
The bill is expected to place new obligations on relevant organisations, including operators of essential services (OES) and digital service providers (DSP), to adopt stronger cybersecurity practices aligned with recognised standards. This includes risk assessments, mandatory event logging, and staff training. Oversight is expected to be handled by sector-specific regulators, with enforcement frameworks defined following final legislation and guidance.

Infographic mapping the main sectors covered by the bill: energy, healthcare, transport, public sector, and more.
For defence and government agencies, compliance includes not only technical provisioning (firewalls, segmentation, encryption) but operational policies such as secure onboarding for contractors, supply chain vetting, and rigid removable media controls.
Technical and Operational Requirements Explained
Baseline security controls for critical infrastructure
Draft proposals outline a set of minimum technical controls that organisations may be required to implement once the bill is enacted. These align with established standards such as the UK’s Cyber Essentials and ISO/IEC 27001, but often go further. Referenced controls include measures such as network segmentation, multi-factor authentication, endpoint detection, secure remote access, and physical security, consistent with existing best practice frameworks.
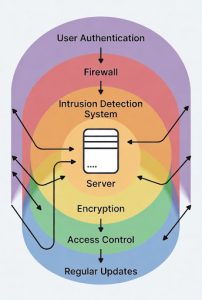
Diagram: Example of multi-layered cybersecurity defences required under the Cybersecurity and Resilience Bill.
Key Takeaways:
- Risk assessments and regular system audits are critical to ongoing compliance.
- Removable media, such as USB drives, require hardware-level scanning and control.
- Incident notification is expected to follow defined timelines, with many proposals aligning to existing seventy-two-hour reporting models used in UK regulation.
Incident detection, response, and reporting
Organisations must have clear incident response processes that cover both detection and containment. Policy discussions around the bill reference incident reporting timelines aligned with existing frameworks such as GDPR, where significant incidents are typically reported within seventy-two hours. In 2023, rapid reporting enabled the UK National Cyber Security Centre (NCSC) to stop 37% of targeted ransomware attacks in progress (NCSC Annual Review 2023).
Human factor and ongoing training
Technological controls are necessary, but the bill also emphasises human behaviour. Proposals place strong emphasis on regular cybersecurity training for all staff, reflecting evidence that human factors remain a primary cause of breaches., as studies indicate that over 80% of breaches involve human error or social engineering (Verizon Data Breach Investigations Report, 2024). As a result, policies must focus on fostering a security-aware culture.
Removable media and usb cybersecurity in industrial and defence environments
The bill places increased emphasis on safeguarding against removable media risks, particularly in high-assurance environments. For example, USB cybersecurity is prioritised in operational technology (OT), manufacturing, and defence contexts. This is because USB devices have historically carried threats into air-gapped and controlled systems. According to industry experts, deploying hardware-based scanning stations can mitigate such risks by physically isolating and cleaning USBs before connection.
For further details on USB cybersecurity strategies and policy implementation, see our comprehensive USB cybersecurity resource.
Practical Impact and Implementation for UK Organisations
Real-world implications for targeted sectors
For energy, utilities, transport, and health sectors, compliance with the Cybersecurity and Resilience Bill will shape not only IT and information security but also the safety and continuity of operational systems. Marrying cybersecurity with physical resilience is now a regulatory imperative.
Key Takeaways:
- Operational disruptions from non-compliance can expose organisations to severe penalties, including fines and regulatory action.
- The bill incentivises cyber risk management investment and cross-departmental collaboration.
- Resilience is measured by both the speed of incident response and the continuity of essential services.
Comparing compliance: before and after implementation
| Key Area | Before Bill | After Bill |
| Incident reporting | Discretionary, varied by sector | Mandatory, with 72-hour notification |
| Removable media policy | Largely advisory, inconsistent enforcement | Standardised hardware and process requirements |
| Staff training | Periodic and role-based | Annual, mandatory for all staff |
| Penalties | Low or sector-specific | Heavy fines and regulatory orders |
Sector-specific application: Defence, CNI, and industry
In sectors such as defence and critical national infrastructure, the bill’s prescriptive approach recognises the severe consequences of a breach. Defence systems face targeted attacks by advanced persistent threats (APTs) using sophisticated removable media payloads. The bill urges high-assurance verification—multi-engine scanning, network isolation, and audit logging.
Case study: Energy sector USB-borne attack
- A UK-based power utility experienced a malware outbreak via a contractor’s USB drive in 2022, resulting in a 12-hour control room outage.
- Post-incident review found insufficient removable media controls and the absence of scanning hardware at entry points.
- With the bill, adoption of dedicated scanning kiosks and policy reinforcement would have significantly reduced incident impact.
This case highlights the necessity for sector-tailored risk controls and continual review.
Assessing compliance and operational readiness
Organisations can benchmark their progress towards compliance through regular audits, tabletop exercises, and simulated incident response drills. External assessments—such as penetration tests and red teaming—are encouraged under the bill’s guidance. Success is measured by swiftness and effectiveness of response, not simply policy existence.
| Compliance Activity | Frequency | Responsible Role |
| Risk assessment | Annual or after a significant change | CISO / IT security lead |
| Incident response drill | Twice per year | Incident response team |
| Staff cyber awareness training | Annually (minimum) | HR / Security training lead |
| Removable media audit | Quarterly | Facilities / IT operations |
“Building resilience into operational processes and culture is as essential as any technical investment,” emphasises Professor Kevin Jones, Cybersecurity Chair at Cranfield University.
Organisational adaptation: Barriers and solutions
Cultural resistance and lack of cyber expertise are the most reported barriers to implementation (CIISec UK Survey, 2024). To address this, the bill recommends phased adoption—starting with critical controls and expanding to organisation-wide coverage. Integrating security by design and appointing dedicated cyber leads in each department are effective, practical steps.
- Solutions include:
- In-house and external cyber training programmes for all roles
- Automated asset discovery and risk scoring
- Deploying hardware-based USB cybersecurity and removable media control stations
- Engagement with sector-specific information-sharing partnerships
Success metrics should track reduction in incidents, staff awareness levels, and mean time to recovery (MTTR) after cyber events.
ROI of bill-driven investments
As of November 2024, the UK Government estimated that full compliance with the bill could reduce cyber-related operational incidents by up to 35% and deliver annual cost savings exceeding £430 million to CNI sectors (Source: UK Parliament, 2024). By minimising downtime, data loss, and reputational harm, the bill is projected to rapidly pay for itself.
- Personalised example: For a 1,000-employee manufacturing firm, adopting hardware-based USB cybersecurity reduces malware risk to production lines—typically avoiding costs of at least £120,000 per incident.
- For smaller municipalities, compliance with the bill makes it possible to qualify for new government cyber grants, supporting digital transformation at reduced financial risk.
FAQ: People Also Ask About the Cybersecurity and Resilience Bill
What is the main purpose of the Cybersecurity and Resilience Bill?
The main purpose of the bill is to establish consistent minimum cybersecurity standards across essential sectors, ensuring organisations can both prevent cyber incidents and recover rapidly if attacked. Its goal is to increase national resilience and accountability.
Who must comply with the bill’s requirements?
Operators of essential services (such as energy, healthcare, water, and transport), government entities, and key digital service providers must comply. Smaller suppliers may also be required to adhere if they form part of critical supply chains.
What are the penalties for non-compliance?
Penalties for non-compliance can include substantial fines, regulatory orders to remediate deficiencies, and, in some cases, public disclosure of lapses. Financial penalties are expected to be proportionate to sector risk and incident severity, with exact figures confirmed following legislative approval.
How does the bill address USB cybersecurity risks?
The bill highlights the importance of rigorous removable media controls, with hardware-based scanning solutions increasingly referenced as best practice in industrial, defence, and OT environments. This prevents malware from crossing into critical systems, especially in industrial and defence settings.
Will the bill affect small and medium-sized businesses?
While the primary focus is on essential service providers, small businesses connected to critical supply chains may be impacted. Many SMEs may benefit from government guidance and funding for security improvements as part of the bill.
How can organisations prepare for compliance now?
Organisations should begin by conducting a cybersecurity gap analysis, reviewing policies against the bill’s requirements, and prioritising high-impact controls. Investing in incident response, staff training, and hardware security measures is strongly advised.
Does the bill introduce new requirements for staff training?
Yes. The bill makes annual cyber awareness training mandatory for all employees. It also encourages sector-specific modules and regular assessment to ensure practical understanding and phishing attack resistance.
What is the timeline for implementing the bill’s provisions?
The bill has progressed through parliamentary scrutiny, with implementation timelines dependent on final legislative outcomes and secondary regulations. Phased adoption is expected once sector-specific guidance is issued. Some critical controls will require immediate adoption in the highest-risk sectors.
Conclusion: Building a Secure, Resilient Future
The Cybersecurity and Resilience Bill marks a pivotal shift in the UK’s approach to defending against cyber threats. By requiring a harmonised approach to risk management, technical controls, and organisational readiness across all critical sectors, the bill sets a high but achievable bar for resilience. In my experience, proactive engagement now gives organisations a clear competitive and risk-reduction advantage.
If you’re looking to strengthen your USB cybersecurity and prepare for forthcoming compliance requirements, explore our practical resources and guidance for safeguarding your critical operations.

